Lookout Security researchers discovered new malicious adware in android application.This malware is spreading through the popular android application and worst part is "it already infected more than 20,000 android application".
Security experts at Lookout dubbed this adware as Shuanet. After research and analysis experts said Trojanized Adware is spreading through the trojanized versions of popular Android apps .Even android application protected with two-factor authentication are also infected with Shuanet.Some of the android application infected with shuanet are given below:
- Candy Crush
- GoogleNow
- Snapchat and many more
Shuanet is able to gain root access to the infected device phone without the user’s knowledge, the threats install themselves as system service applications and are very hard to remove from the devices.
The Lookout Researchers said that this ,Trojanized adware Shuanet are distributed through third-party repositories.
The trojanized versions of the mobile apps are fully functional, for this reason, they don’t raise suspicion. It is important to note that threat actors behind the campaign avoided compromising antivirus apps, a circumstance that suggests a high level of planning when creating these malware campaigns.
“Lookout has detected over 20,000 samples of this type of trojanized adware masquerading as legitimate top applications, including Candy Crush, NYTimes, Okta, WhatsApp, and many others.”
Lookout’s Michael Bentley wrote in a blog post. “Malicious actors behind these families repackage and inject malicious code into thousands of popular applications found in Google Play, and then later publish them to third-party app stores.”
“While historically adware hoped to convince the user to install new applications by showing banners and annoying pop ups, now it can install these third party apps without user consent. In this way it can heavily capitalize on the Cost Per Install paid out by web marketing companies,” Lookout’s Michael Bentley said in a blog post.
“Unfortunately, should the revenue model change on clicks-per-install and ads, this may lead to malware authors using this privilege escalation for new monetization strategies.”
According to the experts, it is easy to predict that this type of trojanized adware will become even more sophisticated over the time.“We expect this class of trojanized adware to continue gaining sophistication over time, leveraging its root privilege to further exploit user devices, allow additional malware to gain read or write privileges in the system directory, and better hide evidence of its presence and activities.”
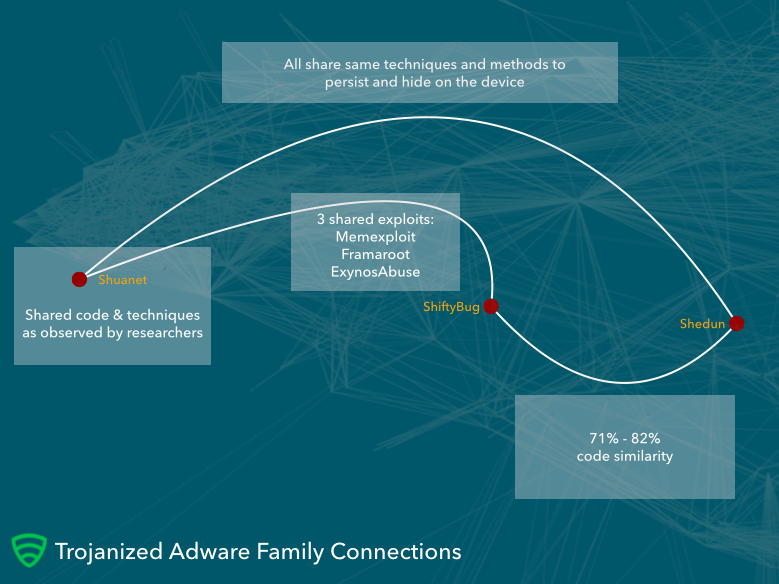
Kemoge and Shuanet adware share at least three exploits to root devices.
The expert observed the majority of the Shuanet adware infections in the United States, Germany, Iran, Russia, India, and Indonesia.
Lookout researchers believe that threat actors behind the adware campaigns Kemoge, Shedun and Shuanet are different groups, anyway the adware families appear to be linked.
In some cases, the variants of malware analyzed share between 71 and 82 percent of their code, a circumstance that suggest the authors used the same pieces of code to build their versions of the auto-rooting adware.