CloudFlare firms revealed that one of its customers was recently hit by a distributed denial-of-service (DDoS) attack that appeared to leverage a mobile ad network and malicious JavaScript.The experts explained that the DDoS attack relied on a JavaScrip that generates legitimate HTTP requests.
Unfortunately, this kind of DDoS attack is being popular in the hacking community, in April security researchers from the University of California at Berkeley and the University of Toronto have discovered a powerful weapon of the Chinese Government cyber arsenal, dubbed the Great Cannon, used to hit websites with powerful DDoS attacks. The Great Cannon has been used by Chinese authorities to knock-out two anti-censorship GitHub pages and it can be also used as a hacking tool to silently install malware on the targeted machine.
The experts explained that the Great Cannon relies on malicious JavaScript injected into unencrypted traffic in order to carry on DDoS attacks.
Another similar DDoS attack was unveil last week, experts at Imgur discovered that a vulnerability in the platform was exploited by attackers to target the imageboards 4chan and 8chan.
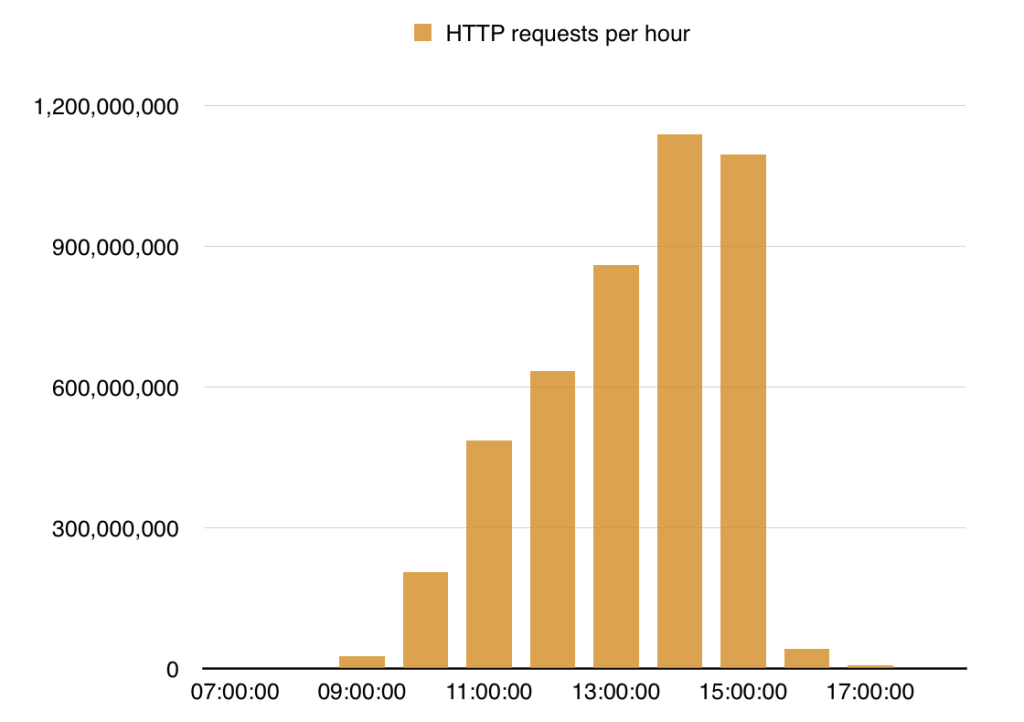
Now, CloudFlare noticed a large number of HTTP requests addressing one of its customer’s website, the DDoS attack peaked at over 1 billion requests per hour. The experts observed a total of 4.5 billion requests reaching the content delivery network’s servers on the day of the attack.
The overall number of unique IP addresses originating the requests is 650,000, 99.8 percent these are from China.
Experts at CloudFlare said,nearly 80 percent of the requests were from mobile devices.
“Attacks like this form a new trend,” states a blog post published by CloudFlare. “They present a great danger in the internet — defending against this type of flood is not easy for small website operators.”
“There is no way to know for sure why so many mobile devices visited the attack page, but the most plausible distribution vector seems to be an ad network,” Majkowski wrote. “It seems probable that users were served advertisements containing the malicious JavaScript. [These] ads were likely showed in iframes in mobile apps, or mobile browsers to people casually browsing the internet.” explained the researcher Marek Majkowski.
CloudFlare researchers excluded that the DDoS attack was conducted by injecting TCP packets like observing in the DDoS attack conducted by the Great Cannon.
CloudFlare provided the following description for the attack scenario:
- A user was casually browsing the Internet or opened an app on the smartphone.
- The user was served an iframe with an advertisement.
- The advertisement content was requested from an ad network.
- The ad network forwarded the request to the third-party that won the ad auction.
- Either the third-party website was the “attack page”, or it forwarded the user to an “attack page”.
- The user was served an attack page containing a malicious JavaScript which launched a flood of XHR requests against CloudFlare servers.
“It seems the biggest difficulty is not in creating the JavaScript — it is in effectively distributing it. Since an efficient distribution vector is crucial in issuing large floods, up until now I haven’t seen many sizable browser-based floods,” Majkowski added.