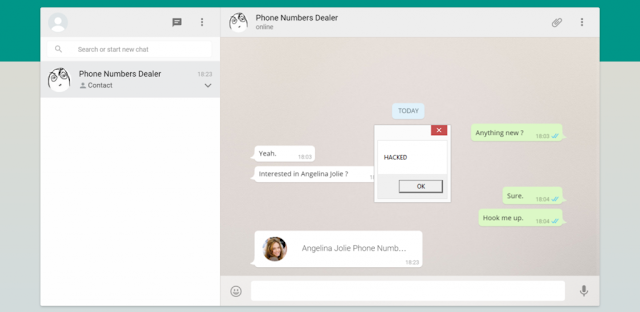
According to the security firm Check Point, vCard flaw in Whatsapp web could exposed the 200 million of whatsapp web users. VCard flaw allow the attacker to run arbitrary code in the web based version of whatsapp.
Whatsapp web is the web based extension of Whatsapp application.This will sync all the sent and received message between whatsapp application and and web based extension and WhatsApp Web based extension is available for most WhatsApp supported platforms, including Android, iPhone, Windows,etc...
How attack works?
Kasif’s said,an attacker need to inject the malicious code into VCard and send the VCard to victim.Once victim open the file,it will automatically start downloading the malicious code into victim machine.Further it also let the attacker to distributing bots, ransomware, RATs, and other malwares. By manually intercepting and crafting the xmpp could allow to control the extension of vcard file.
How VCard File is designed to execute the malicious code?
Researchers injected the malicious payload command in the name section of the vcard file separated by the ‘&’ character and changed the file extension to ".bat".When victim click on the file,Windows will attempt to run all lines in the files, including our controlled injection line which will force to start downloading the malicious file.Download file contain the following code:
Further researchers tried to execute ".exe" files through same scenario but without XMPP interception.For this,researchers examined the communication protocol of whatsapp and found that whatsapp using open standard Extensible Messaging and Presence Protocol.
After examining the protocol,researcher binded the ".exe" in the vcard files to target the victim. WhatsApp web client allow to download and run the ".exe" file too.Check Point added that attackers can also use an icon to exploit the flaw and serve malicious binaries.